Mariners Urged to Get In Front of Growing Threat
Before any vessel gets ready to head out to sea, shore-based personnel and onboard crew run down a lengthy list of safety, compliance and regulatory checks, all part of a standard risk management exercise. What’s often not on that list is an invisible, but looming risk that if ignored, could leave ships off course, off schedule or even dead in the water, thanks to infected computer systems, phony or corrupted charts and blocked communications signals.
Cyber crime has come of age in the maritime sector. Observers like Futurenautics claim the maritime industry is actually “overexposed” when it comes to cyber risk management. From modern vessels virtually run by massive doses of technology and limited crew, to older ships chugging along with out-of-date and insecure applications, all are vulnerable in their own way to the stealth threats to shipping security and safety. The seeming lack of awareness among companies, if not their crews, has many government, security and industry organizations very concerned, and very anxious to help the industry get out in front of this looming problem.
The last two years has seen a flurry of activity around cyber security. With zero funding, the U.S. Coast Guard pulled about 80 personnel with the necessary security and IT credentials out of other units to form the U.S. Coast Guard Cyber Command. Last August, it released a Cyber Security strategy paper, which provides a framework and a 10-year plan designed to reduce risk to the maritime cyber critical infrastructure.
Industry alliances, including BIMCO, CLIA, Intertanko, Intercargo, ISC and others, recently published “The Guidelines on Cyber Security Aboard Ships,” a blueprint for companies seeking to aggressively address cyber security. Separately, Insurers Marsh & McLennan Companies published a cyber security report targeted at educating executives, while Futurenautics surveyed 3,000 crewmen on their experiences with cyber attacks. Last December, International Association of Classification Societies (IACS) leadership added cyber security as the third pillar of its oversight, alongside hull and machinery, and talked about creating a cyber system safety framework.
Where’s the Fire?
What could possibly happen to a vessel out in the middle of the ocean? A lot, actually, thanks in part to the industry’s increasing reliance on technology. A look at the incidents reported so far – ranging from fake charts and invoices, to drug smuggling, to compromised rigs and ship systems – is just the tip of the cyber iceberg lying in wait for a modern-day unprepared Titanic, worry security experts.
The attacks run the gamut, employing phishing, social engineering, malware, viruses, worms, denial of service, keystroke capture, skimmers, Trojans, ransomware, signal jamming, identity, manifest and corporate data theft, cargo diversion and smuggling, phony bills, etc. While SATCOM vendors like KVH and Bluetide Communications enable clients to block web sites, divvy up and even physically separate internet bandwidth to meet business, personal and entertainment demands, it’s not enough to bar the cyber door. One unsettling truism is that hackers are always a generation or two ahead of their victims.
Crew data, financial data, cargo manifests and high value cargoes are all at risk. Fake invoices are said to be epidemic in the bunker fuel sector. From a safety standpoint, protecting and backing up your electronic navigation systems and GPS signal will be key.
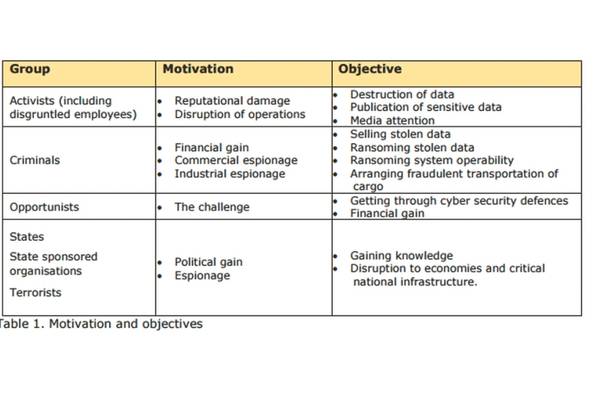
A wide range of players, from criminal syndicates looking for money; to political or environmentalist hacktivists bent on making a statement or stopping a company’s activities; to corporate and nation-state espionage that seeks to steal information and cripple economies; and even just lone wolves looking to build street cred or test their skills, are all in on it. And they don’t need to be particularly sophisticated. Attacks can be outsourced to hackers for hire, the new career path on the dark side.
Your Own Worst Enemy
It might surprise some, but the cyber security community sees employees both as a bigger problem than technology, and the key to success. The SANS Institute, a bellwether provider of security training, has a program devoted to “securing the human.” Unintentional or accidental incidents are actually more of a threat than deliberate sabotage or outside perpetrators. This is no minor issue when crew connectivity to the outside world is now ‘de rigueur’ for recruitment and retention.
“You have a better chance of securing technology than educating and making sure humans do the right thing,” observes Kim Hall, CLIA Director of Technical & Regulatory Affairs for Operational & Security. In one case, as a vessel was getting ready to go to sea, the first mate decided to listen to some music. He plugged his unbeknownst to him infected player into the ship USB port, unleashing an infection. The ship had to cool its heels in port for two days waiting for a technician to come and fix the problem. It’s why the U.S. Navy and Coast Guard banned personal USB flash drives. Some companies seal up USB ports on ship computers to prevent such accidents.
But sometimes the problem is the technology itself. It doesn’t matter how old or new your ships’ systems are – nothing is safe. The more automated a vessel is – the more the bridge operates as the proverbial “brain” of the ship – the more susceptible the entire operation is to malfeasance. Autonomous ship operators of the future will have to deal with issues when something goes wrong. Not everything can be handled or discovered remotely.
The technology issue facing older vessels is more critical, and correcting it urgent. Running applications that were never meant to be networked or linked to the internet, it’s not uncommon to have wide open back doors, created to enable remote monitoring and repairs but with little thought given to criminal egress. And, many applications were written on operating systems that are no longer supported, and hence, no longer secure. And patching solutions can aggravate the problem.
Pressure to Act is Building
Emil Regard, Managing Director, BlueTide Communications, which recently debuted Security-As-A-Service for remote network monitoring and security, says “There are only two kinds of computers: Those that have been hacked, and those that will be hacked.” Ask any major government agency, financial center, retailer, healthcare giant or insurer. Nothing, and no one, is safe.
The majority of insurance policies that cover ships and ports include cyberattack “Exclusion Clauses.” For now, most insurers focus on creating awareness and working with clients to help them get started on battening down the cyber hatches.
Allianz educates clients by speaking on topics of cyber threats and through educational papers. “The U.S. is about to launch a ‘Know the Facts’ series on cyber to help our brokers (and subsequently clients) understand current exposures, risks, and coverage issues. This will be a quarterly feature,” says Emy R. Donavan, Head of Commercial Cyber, North America, Allianz.
Some insurers are looking into offering some level of policy protection. Allianz is finalizing a cyber security policy that will offer coverage for liability associated with data breach, costs of complying with regulatory requirements, digital asset replacement costs, cyber extortion and other coverage. “Coverage at this time is only available for larger clients with a reasonable level of risk management around cyber threats. We will be launching a mid-market initiative later in the year, but that will still require some basic cyber hygiene responses on the application,” says Donovan.
Regulatory Sword
If that doesn’t get your attention, then the specter of more regulation might. That’s because, at some point, taking steps to implement a cyber security program might become a necessary part of proving seaworthiness. Capt. Andrew Tucci, Chief, Office of Port and Facility Compliance U.S. Coast Guard, thinks the level of regulation, although nothing like the typical IMO iron-clad directives, will be more akin to what industry has done with safety management.
One of the biggest stumbling blocks to manage the risk is that “we don’t know what the threat is,” according to Capt. Michael Dickey, deputy commander, U.S. Coast Guard Cyber Command, noting that the hacking community’s attack methods are constantly evolving. Hence, the maritime community needs to advance flexible guidelines for best practices and program frameworks. The industry-driven “Guidelines on Cyber Security Onboard Ships” is one such effort. One size won’t fit all ships, and cyber security experts agree, it is imperative that future regulations be constructed as a “living document,” so companies can morph their security, keeping pace with trending threats.
“There are enough regulatory documents in the shipping world now,’’ exclaims Philip Tinsley, BIMCO’s maritime security manager. Hoping to update the Guidelines several times annually, his working group is planning to address training, and build in a reporting facility where breaches can be documented. Gathering data is “key to being able to progress,” says Tinsley. BIMCO also wants to add a clause to vessel contracts that will show an owner has addressed the issue.
However laggard it may be, the maritime industry actually has an ace up its sleeve when it comes to building cyber security plans. First, shipping companies excel at risk management. Second, with hundreds of years of safety culture at its back, safety management programs are in place on most vessels. The best practices for managing the cyber threat are straightforward, and akin to the thinking and steps that go into building an SMS. And who hasn’t rowed that boat?
It’s Complicated
And yet cyber risk management is a little more complicated than that. Gideon Lenkey, director of technology for EPSCO-Ra, which recently launched a full suite of managed cyber security network services, says there are companies that employ best practices and pass regulatory audits – and yet their security is bad. “They are compliant, but they are a soft target.” Conversely, he cites companies that were not technically complaint, but their security practices were good. “I would hate for someone to think things are under control because they have met some minimum business practices.”
“And if you think you are safe because no one has ever heard of you, that’s no protection at all. The worst mistake someone could make perhaps is to somehow convince themselves, ‘I have no risk,’’’ says the Coast Guard’s Tucci.
Kim Hall, CLIA Director of Technical & Regulatory Affairs for Operational & Security, points out that it is not enough to secure individual systems or personal devices. “Looking at cyber security as a separate system ignores that it is part of an interdependent and interconnected system.” A good security plan must look at the entirety of the system and where parts interface internally and externally, including to third parties.
And yet a new study, “Tone at the Top and Third-Party Risk’’ conducted by Ponemon Institute LLC, found that while companies understand the third party security risk, it is rarely a primary risk management objective – a costly error. “In the past 12 months, organizations represented in this research spent an average of approximately $10 million to respond to a security incident as a result of negligent or malicious third parties.’’
Start at the Top
Cyber risk is not an IT issue. Managing the cyber threat is also difficult, not because the proven, technical solutions aren’t there, but because the best laid plans mean nothing if nobody’s following through. “It has to start with the leadership first – if they aren’t willing to effect change – you can’t educate employees,” says Michael Crean, CEO, Solutions Granted, and Bluetide Communication’s security partner.
“[Cyber risk] is a board-level governance issue which requires the engagement of the full executive leadership team to address. Effectively managing cyber risk today ... requires a comprehensive, multi-dimensional approach that looks at people, processes and vendors – and includes response and recovery plans in addition to prevention tactics,” said John Drzik, chairman, cyber risk working group, for insurers Marsh & McLennan Companies, in that organization’s “Cyber Risk Handbook 2015.”
Coincidently, one of the top concerns coming out of a cyber security roundtable hosted by KVH Industries at CMA Shipping 2016, was complacency by ship operators. The panel identified a need for training, contingency plans for dealing with a cyber attack, and a set of best practices for minimizing risks.
Once executives are on board, it’s time to pull in the crew. Creating awareness involves more than giving employees a heads up that cyber crime is heading out to sea. It’s letting them know that a successful infiltration is only a click away, that they themselves can inadvertently be the ships’ own worst cyber enemy.
Another option is to takes the “What’s in for me” tack. One of the best approaches is to educate from a personal and family impact. The idea is to teach them how to protect their personal data and identities online, how to keep viruses and malware out of their computers. You talk to them about creating multiple, strong passwords; about how not to click on links, download or open email from sites or people they don’t know. Then, you throw in, “Oh by the way, these same tips will help keep ship – and you – safe, as well,”
A New Light
Creating awareness and correcting behavior that can create vulnerabilities is paramount. But there’s more to it than that. All crewmembers have to add the cyber threat to the way they think about risk management. Unlike most safety violations or physical acts of crime, cyber attacks aren’t visible. You won’t see the launch of a denial-of-service attack or malware wending its way through your computer network. And while people will respond quickly to correct a safety violation, they are a lot less likely to say anything if they see a shipmate plug a personal device into the ships’ USB port, or flip to a web site while working on a ship’s computer.
This means also avoiding being lulled into a false sense of security by technology that appears to be working. For instance, false or corrupted charts can lead a ship dangerously off course. “We need to tell people to get up out of the chair with a pair of binoculars and go look over the side every once in a while,” says Capt. Dickey. There is also a movement afoot to return to decidedly non-technical back up plans – paper documentation and charts, and the century old art of navigating by the heavens. “You can’t hack a sextant,” quips Dickey.
It doesn’t help that crews can be comprised of multiple nationalities and languages, says Lance M. Savaria, managing director/partner, EPSCO-Ra Ltd. Or that the ships themselves are mechanically and technologically unique – even two of the same class of vessel owned by the same company doing the same job will have differences. Training and the actual security plan, must be customized for each particular vessel.
Protect, Detect, Assess & Respond
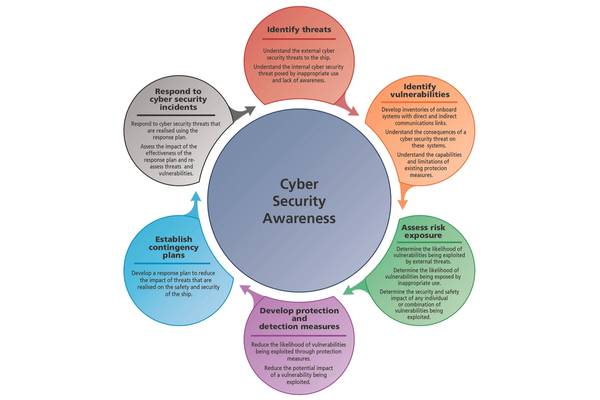
This is no time to panic. There is plenty of agreement on the steps to take and a wealth of free sources for guidance. Whether you buy into the theory that cyber security is just another branch of safety management, or a unique area of concern, the same steps used to build a SMS program on board apply here, with a few twists. The blueprint includes:
- Self-assess the ship’s cyber “hygiene.”
- Locate and address vulnerabilities, install appropriate cyber defense technologies as appropriate, keep ship and crew technology as separate as possible.
- Secure an outside assessment and audit, including penetration testing
- Implement a policy that covers acceptable use of allowed personal and ship technology, that encourages incorporation of a cyber threat into any problem assessment, that supports and encourages crew to report possible breaches.
- Make the crew cyber risk aware and provide training on safe and responsible use of technology, what anomalies should raise a flag, and provide regular risk updates and drills.
- Disseminate your policy and safety measure to your vendors and other third-parties with the potential to infect your networks.
- Encrypt or use secure channels when communicating sensitive data to port authorities or shore-based offices.
- Formulate a process for recording, reporting and dissecting actual and near misses. Consider sharing the data anonymously with industry groups trying to track attack trends
- Write a contingency plan and build in resilience.
After you’ve done all that, it’s important to stay vigilant. As Hall likes to say, “It’s like Capt. Obvious from Hotels.com – If you are not thinking about how to train folks, making sure your systems are secure and constantly reevaluating – if you are not doing all of this, then you are taking on an unwarranted level of risk.” And as Tinsley notes, “There’s always someone somewhere doing something they shouldn’t, so why chance it?”
Famous and Mundane Breaches and Attacks … at a Glance
What could happen? Oh, what a computer virus, hacking for hire or $30 jammer could do:
- In 2008, the DOD banned the use of removable storage devices in an effort to halt the spread of a computer virus wending its way through the DOD network. Though the ban was later relaxed to allow government-procured and owned devices, civilian flash drives remain verboten by the U.S. Navy and the U.S. Coast Guard because it is impossible to track how they are being used, and there is no way to know whether they are infected – a recipe for impending disaster.
- In 2010, malware overwhelms underway off-shore drilling rig in Asia, forcing a prolonged shutdown. Reportedly the lack of cyber security expertise onboard is the main reason it took a week to identify the cause and fix.
- In 2011, pirates hack into ship servers to identify vulnerable shipments, later boarding it with bar code readers to find the targeted cargo.
- In 2012, a foreign military compromises “multiple systems” onboard commercial ship contracted by U.S. TRANSCOM.
- In 2012, over 120 ships, including major Asian Coast Guard vessels, experience malicious jamming of GPS signals.
- Nation-state cyber attacks are not uncommon; though so far tend to target land-based systems. These include: A computer virus that in 2012 targeted Iranian oil companies, forcing much of the oil infrastructure offline, including Iran’s Kharg Island oil terminal, which handles 80% of its oil exports; a believed-to-be retaliatory 2012 virus attack, said to be the largest ever, on Saudi Aramco, Saudi Arabia’s national oil company, which supplies 10% of the world’s oil, wiping out or destroying the hard drives of at least 35,000 PCs, and costing the company months of work and barrels of money before it could get its delivery tracking and billing system back on line; and Stuxnet, the U.S./Israeli-created virus used to destroy centrifuges in an Iranian nuclear facility in 2010. On an ongoing basis, the North Korean government routinely jams critical GPS signals from at least a 50-mile radius and may be pushing it to 100.
- In 2013, European authorities announce drug smugglers hacked cargo tracking systems in the Port of Antwerp to locate and retrieve their illegal goods. The two-year operation hired hackers to infiltrate computers controlling the movement and location of containers. Malicious software and key-logging devices were used in the plot. No one noticed until containers started to vanish.
- In 2014, a seven-hour GPS signal disruption took a key U.S. port offline, shutting down multiple ship-to-shore cranes for several hours.
- Typical of how insiders can inadvertently muck up the works, a mate on a vessel heading out to sea, plugged his low-on-battery smart phone into a UBS port on the bridge. The resulting malware infection erased or corrupted all the charts on the ECDIS system of the ship’s systems, costing an additional two days in port waiting for a fix.